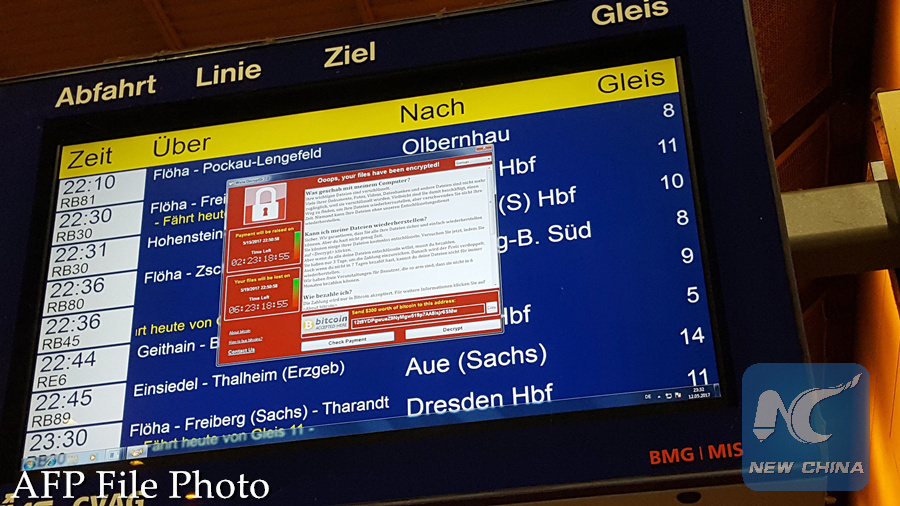
A window announcing the encryption of data including a requirement to pay appears on an electronic timetable display at the railway station in Chemnitz, eastern Germany, on May 12, 2017. (AFP PHOTO)
MOSCOW, May 22 (Xinhua) -- The installation of the official Microsoft patch and security software updates can be an effective way to protect computers from attacks of the WannaCry ransomware, Russian security software company Kaspersky Lab said in a recent interview with Xinhua.
A massive number of organizations across the globe have been targeted by the malware since May 12. Hackers used the Trojan encrypter WannaCry to lock computers and demand a payment for the decryption. So far, it has hit more than 200,000 computers in 150 countries, crippling hospitals, governments and businesses.
WannaCry takes advantage of the Windows exploit known as Eternal Blue which exploits a vulnerability that Microsoft patched in security update MS17-010 on March 14, to gain remote access to users' computers and install malicious driver programs before locking files and demanding a ransom, Kaspersky told Xinhua.
According to a statement provided by Kaspersky, its computer system monitoring tool has detected 11 kinds of such malicious programs that WannaCry uses to encrypt computer files.
The cyber security provider warned against using the means of decryption offered on the Internet or received in emails, as WannaCry's encryption algorithm can not be decoded with existing methods, which, worse still, may cause even greater harm to the infected computer and others connected to it, thus accelerating the propagation.
Currently, the only right approach in case of a WannaCry infection that has been found effective is system reinstallment at the expense of encrypted file, Kaspersky said.
"If you find that your computer has been infected, you should turn it off and contact the information security service for further instruction," Kaspersky said.
Noting that precautions play a crucial part in defending against the WannaCry virus, Kaspersky suggests users install an official patch from Microsoft that closes the vulnerability used in the attack as well as upgrade the security software scanning critical areas at all time to detect potential infection as early as possible.
It is also suggested to create file backup copies on a regular basis and store copies on storage devices that are not constantly connected to the computer.
For computers within corporate networks, once an attack is spotted, disconnection of the invaded computer from the Internet and internal networks needs to be done immediately.
In addition, while unpatched Windows computers can be remotely attacked with the Eternal Blue exploit and infected by the WannaCry ransomware, the lack of existence of this vulnerability doesn't really prevent the ransomware component from working, Kaspersky said.
"Nevertheless, the presence of this vulnerability appears to be the most significant factor that caused the outbreak," it said.
At present, network security companies, including Kaspersky, are developing more effective means of fighting the WannaCry virus and decoding maliciously encrypted files, and relevant information will be released in a timely manner, Kaspersky said.

